Home
Services
About
Contact
01794 377611




At Burton Technologies, we're not just a provider; we're your partner in cybersecurity. We believe in equipping you with the knowledge, tools, and protection you need to thrive in today's digital landscape. Contact us today and let's fortify your cybersecurity, together.
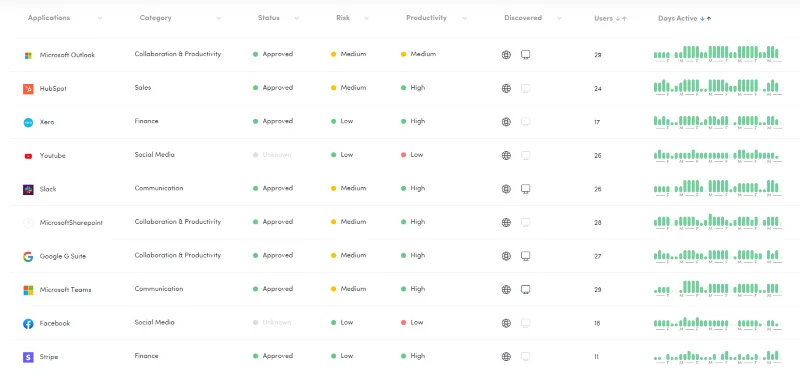
Our not-so-secret weapon in the cybersecurity fight works on a zero-trust basis, effectively blocking everything and allowing what is needed.
It acts as a gatekeeper to prevent anything bad happening on your network and your devices. If you want to block USB devices, not a problem. But, what if you needed a specific USB device to be used in the Social Media team? No worries, we can allow a device based on its serial number and assign it to a group of people.
But, want to stop documents being uploaded or downloaded? Sure! No problem, let's lock that USB device to allowing jpg and png only!
It's a very powerful, but hugely flexible solution to preventing a myriad of threats, from cyber to human, including insider threats.